𝐔𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝𝐢𝐧𝐠 𝐈𝐃𝐒 𝐚𝐧𝐝 𝐈𝐏𝐒: 𝐄𝐧𝐡𝐚𝐧𝐜𝐢𝐧𝐠 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲
In today’s digital environment, Protecting your network from cyberattacks is essential. That’s where Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) come into play.
Before learning about IDS and IPS. The answer to “what is intrusion” is typically an attacker gaining unauthorized access to a device, network, or system.
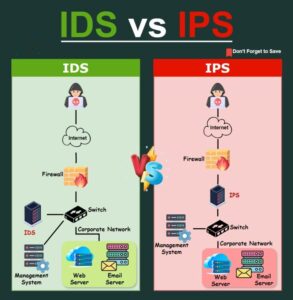
𝐈𝐧𝐭𝐫𝐮𝐬𝐢𝐨𝐧 𝐃𝐞𝐭𝐞𝐜𝐭𝐢𝐨𝐧 𝐒𝐲𝐬𝐭𝐞𝐦 (𝐈𝐃𝐒):
-An IDS is an application that monitors network traffic and searches for known threats and suspicious or malicious activity.
-The IDS sends alerts to IT and security teams when it detects any security risks and threats.
-The IDS is a listen-only device.
-The IDS monitors traffic and reports results to an administrator. It cannot automatically take action to prevent a detected exploit from taking over the system.
𝐓𝐡𝐞𝐫𝐞 𝐚𝐫𝐞 𝐭𝐰𝐨 𝐭𝐲𝐩𝐞𝐬 𝐨𝐟 𝐈𝐃𝐒:
𝟏) 𝐍𝐞𝐭𝐰𝐨𝐫𝐤-𝐛𝐚𝐬𝐞𝐝 𝐈𝐃𝐒 (𝐍𝐈𝐃𝐒): Monitors network traffic in real-time and identifies suspicious patterns.
𝟐) 𝐇𝐨𝐬𝐭-𝐛𝐚𝐬𝐞𝐝 𝐈𝐃𝐒 (𝐇𝐈𝐃𝐒): Monitors activities on individual computers or hosts for suspicious behavior.
𝐈𝐧𝐭𝐫𝐮𝐬𝐢𝐨𝐧 𝐏𝐫𝐞𝐯𝐞𝐧𝐭𝐢𝐨𝐧 𝐒𝐲𝐬𝐭𝐞𝐦 (𝐈𝐏𝐒):
-An essential part of IPS is the network security technology that constantly monitors network traffic to identify threats.
-The general meaning of IPS, IPS technology is also an intrusion detection prevention system (IDPS).
-IPS solutions are also very effective at detecting and preventing vulnerability exploits.
𝐁𝐞𝐧𝐞𝐟𝐢𝐭𝐬 𝐨𝐟 𝐈𝐃𝐒 𝐚𝐧𝐝 𝐈𝐏𝐒:
-Enhanced Security Posture
-Real-time Threat Response
-Regulatory Compliance
𝐊𝐞𝐲 𝐃𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞𝐬:
-𝐅𝐮𝐧𝐜𝐭𝐢𝐨𝐧: IDS detects and reports intrusions, while IPS detects, prevents, and responds to intrusions in real-time.
-𝐃𝐞𝐩𝐥𝐨𝐲𝐦𝐞𝐧𝐭: IDS can be deployed passively (out-of-band) to monitor traffic without affecting it, while IPS is typically deployed inline (in-band) to actively block or prevent threats.
-𝐑𝐞𝐬𝐩𝐨𝐧𝐬𝐞: IDS only generates alerts, whereas IPS can take automated actions to block or prevent detected threats.
-𝐅𝐨𝐜𝐮𝐬: IDS focuses on detection, while IPS focuses on prevention.
In summary, while both IDS and IPS serve to enhance network security, IPS offers a more proactive approach by actively preventing intrusions in real-time, whereas IDS primarily focuses on detection and reporting.