𝐔𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝𝐢𝐧𝐠 𝐈𝐃𝐒 𝐚𝐧𝐝 𝐈𝐏𝐒: 𝐄𝐧𝐡𝐚𝐧𝐜𝐢𝐧𝐠 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲
9 June, 2024
Admin
0 Comments
CCNA Training In Noida
𝐔𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝𝐢𝐧𝐠 𝐈𝐃𝐒 𝐚𝐧𝐝 𝐈𝐏𝐒: 𝐄𝐧𝐡𝐚𝐧𝐜𝐢𝐧𝐠 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲
6:24 pm
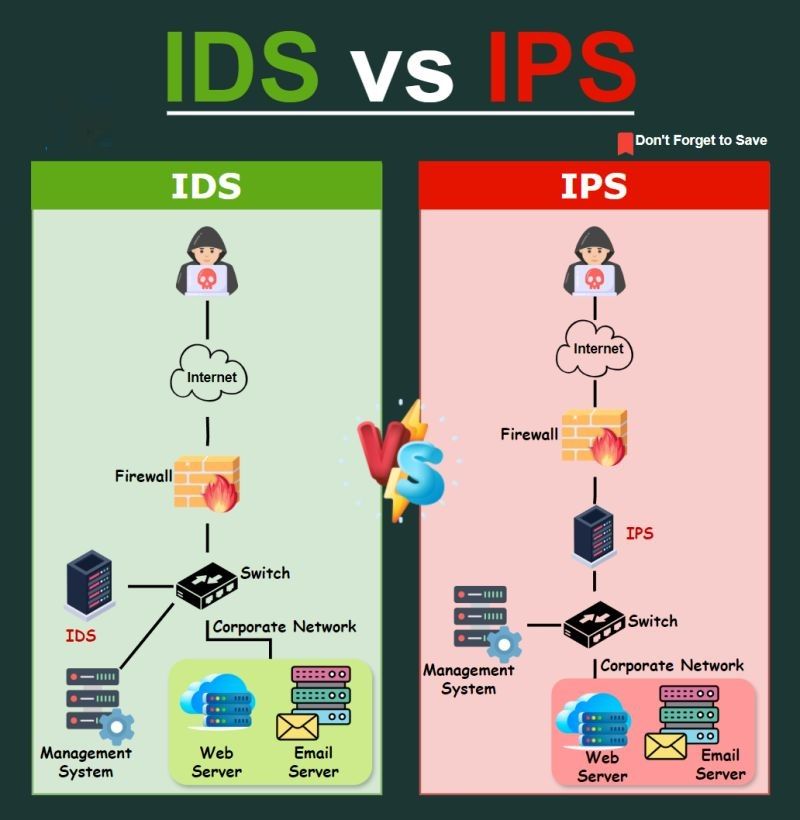
𝐔𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝𝐢𝐧𝐠 𝐈𝐃𝐒 𝐚𝐧𝐝 𝐈𝐏𝐒: 𝐄𝐧𝐡𝐚𝐧𝐜𝐢𝐧𝐠 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 In today’s digital environment, Protecting your network from cyberattacks is essential. That’s where Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) come into play. Before learning about