Top CCNA Interview Questions
1. Explain OSI Layer?
Open system interconnect (OSI) was developed by the international organization for standardization (ISO) and introduced in 1984.
It’s a consists of seven layers
Application layer, Presentation layer, Session layer, Transport layer, Network
layer, Data link layer, Physical layer.
2. Which Layer is Responsible for Reliable Connection?
The transport layer guarantees a reliable end-to-end connection
3.What are Different protocol works at each of the Layer in OSI model?
Application layer
It’s responsible for providing an interface for the user to interact with application
services or network services.
Ex-Web browser (HTTP), Telnet
Presentation layer
It’s responsible for defining a standard format to the data.
The major functions described at this layer are: –
Encoding-Decoding
Ex- AVI-(video), WAV-(voice), JPEG (graphite), ASCII (text) Encryption-Decryption
Session layer
It’s responsible for establishing, maintaining, and terminating the sessions.
Session ID is used to identify a session or interaction.
Ex-Remote procedural call, Apple talk session protocol
Transport Layer
It provides data delivery mechanism between applications in the network.
Transport layer is the major function layer In OSI layer
Identifying service
Multiplexing & De-multiplexing Segmentation,
Error correction, flow control Transport layer
protocols?
The protocols which take care of data transport at transport layer are TCP/UDP
Different between TCP/UDP
TCP UDP
Transmission Control Protocol User datagram protocol
Connection Oriented Connection less
Support acknowledgements No support for acknowledgements
Reliable communication Unreliable communication
Protocol no.6 Protocol no.17
Ex-HTTP, FTP, SMTP DNS, DHCP, TFTP
Network Layer
It provides logical addressing path determination (routing)
The protocols that work in this layer are: -Routed Protocol, Routing Protocol Routed Protocols Used to carry
user data between data. Routing Protocols used performs path determinization routing.
Data link layer
It provides communication with network layer.
Mac (media access control) it provides reliable transit of data across a physical link.
Physical layer
It defines the electrical, mechanical functional specification for communication between the network devices
5. What is the port number and give some examples?
A port number is a way to identify a specific process to which an Internet or other network
message is to be forwarded when it arrives at a server. For the Transmission Control Protocol
and the User Datagram Protocol, a port number is a 16-bit integer that is put in the header
appended to a message unit.
• FTP-File Transfer Protocol (TCP-20,21)
• SSH-Secure Shell SSH Secure Login (TCP-22)
• Telnet remote login service, unencrypted text messages (23)
• SMTP-Simple Mail Transfer Protocol E-mail routing (TCP-25)
• DNS-Domain Name System (TCP/UDP-53)
• DHCP-Dynamic Host Configuration Protocol IP-(67server)-68(client).
• HTTP-Hypertext Transfer Protocol (TCP-80) used in the World Wide Web (TCP- 80)
• POP3-Post Office Protocol POP3 (TCP-110)
• NTP-Network Time Protocol (UDP-123)
• SNMP-Simple Network Management Protocol (UDP-161/162)
• HTTPS- Secure (HTTPS) HTTP over TLS/SSL(TCP-443)
6. What is the range of port Number?
Well known Ports – 0 to 1023
Registered Ports-1024 to 49151 Open
Poerts-49152 to 65535
7. What is a Protocol Number and give some examples?
The protocol number is a single byte in the third word of the datagram header. The value identifies the protocol in the layer above IP to which the data should be passed.
Protocol Protocol Number
• ICMP ——————— 1
• IGMP ——————— 2
• IPV4 ———————– 4
• TCP ———————— 6
• EGP ———————— 8
• IGP ————————- 9
• UDP ———————- 17
• IPV6 ——————— 41
• GRE ———————– 47
• EIGRP ——————— 88
• OSPF ——————— 89
• BGP ———————– 179
8. What is the Unicast, Multicast and Broadcast?
Unicast: In computer networking, unicast is a one-to-one transmission.
Multicast: In computer networking, multicast is group communication.
Broadcast: In computer networking, one-to-many
9. What is the different between Half-duplex and Full duplex?
Half Duplex-Data can flow in both direction but not simultaneously. At a time, Data can flow only in one directional Ex-HUB.
Full Duplex-Data can flow both directional simultaneously-Switch.
10. What is the MAC format?
It is a 12 Digits 48 Bit(6byte) Hardware address written in Hexadecimal format. It
consists of two parts: –
• The first 24 Bits OUI (Organizationally Unique Identifier) is assigned by IEEE.
• The last 24 Bits is Manufacturing-assigned Code.
11. What is a Frame?
The Data link layer formats the message into pieces, each called a data frame and adds a customized header containing the hardware source and destination address.
12. What is the TCP/IP Model?
TCP/IP is four-layer standard model.
The four layers of TCP/IP model are: -Application layer, Transport layer, internet layer, Network access layer.
13. What are the protocols that are include by each layer of the TCP/IP model?
• Application layer-DNS, DHCP, FTP, TFTP, SMTP, HTTP,Telnet,SSH.
• Transport layer-TCP, UDP
• Internet layer-IP, ICMP, IGMP
• Network access layer-Ethernet, Token Ring, FDDI,X.25,Frame Relay,ARP,RARP.
ARP (Address Resolution Protocol)
14. What is the ARP?
Address Resolution Protocol (ARP) is a network protocol, which is used to map a network layer protocol address (IP address) to a data link layer hardware address (MAC address). ARP basically resolves IP address to the corresponding MAC address.
15. ARP work at Which layer and why?
ARP work at the data link layer (layer 2) ARP Is implemented by the network protocol driver
and its packets are encapsulated by ethernet headers and transmitted.
16. What is an ARP Table(cache)?
An ARP cache is a collection of Address Resolution Protocol entries (mostly dynamic) that are created when an IP address is resolved to a MAC address (so the computer can effectively communicate with the IP address) An ARP cache helps the attackers hide behind a fake IP address.
17. What is the size of an ARP request and ARP reply packet?
The size of an ARP request or reply packet is 28 bytes.
18.What is Proxy ARP?
Proxy ARP is the process in which one device responds to the ARP request for another devices.
Ex-Host A send an ARP request to resolve the IP address of Host B. Instead of Host B, Host C responds to this ARP request.
21. What is Reverse ARP?
Reverse ARP is used to obtain the device’s IP address when its MAC address is already known.
22. What is Inverse ARP?
Inverse ARP dynamically maps local DLCIs to remote IP address when frame Relay is configured.
TCP (Transmission Control Protocol)
23. What is (Transmission Control Protocol) TCP?
It is one of the most used protocols within digital network communications and ensures end-to-end data delivery. TCP organizes data so that it can be transmitted between a server and a client. It guarantees the integrity of the data being communicated over a network.
24. Explain TCP Three-Way handshake process?
TCP 3-way handshake is a process which is used in a TCP/IP network to make a connection between the server and client. It is a three-step process that requires both the client and server to exchange synchronization and acknowledgment packets before the real data communication process starts.
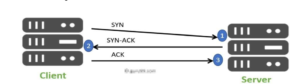
25. What is the propose of RST bit?
When the connection is not allowed by destination connection is reset



